
Protection from Undiscovered Vulnerabilities
Virsec’s patented technologies protect your servers from undiscovered and unpatched vulnerabilities so you always stay protected.
“Virsec virtually patches vulnerabilities in runtime memory, so nobody can exploit them.”
Chief Security Architect
Schneider Electric
Stop Fileless Memory Attacks
AITE Group
Protect Legacy Applications
Eliminate Ransomware Threats
Stop Supply Chain Poisoning
Virsec Security Platform (VSP) Highlights
VSP does this by instantly mapping the application workload when it launches, in a matter of milliseconds, and deterministically allowing only known good behavior.
Deterministic Threat Approach
Does Not Require Access to Source Code or Data
Zero Dwell-Time Defense
No Impact on Application Performance
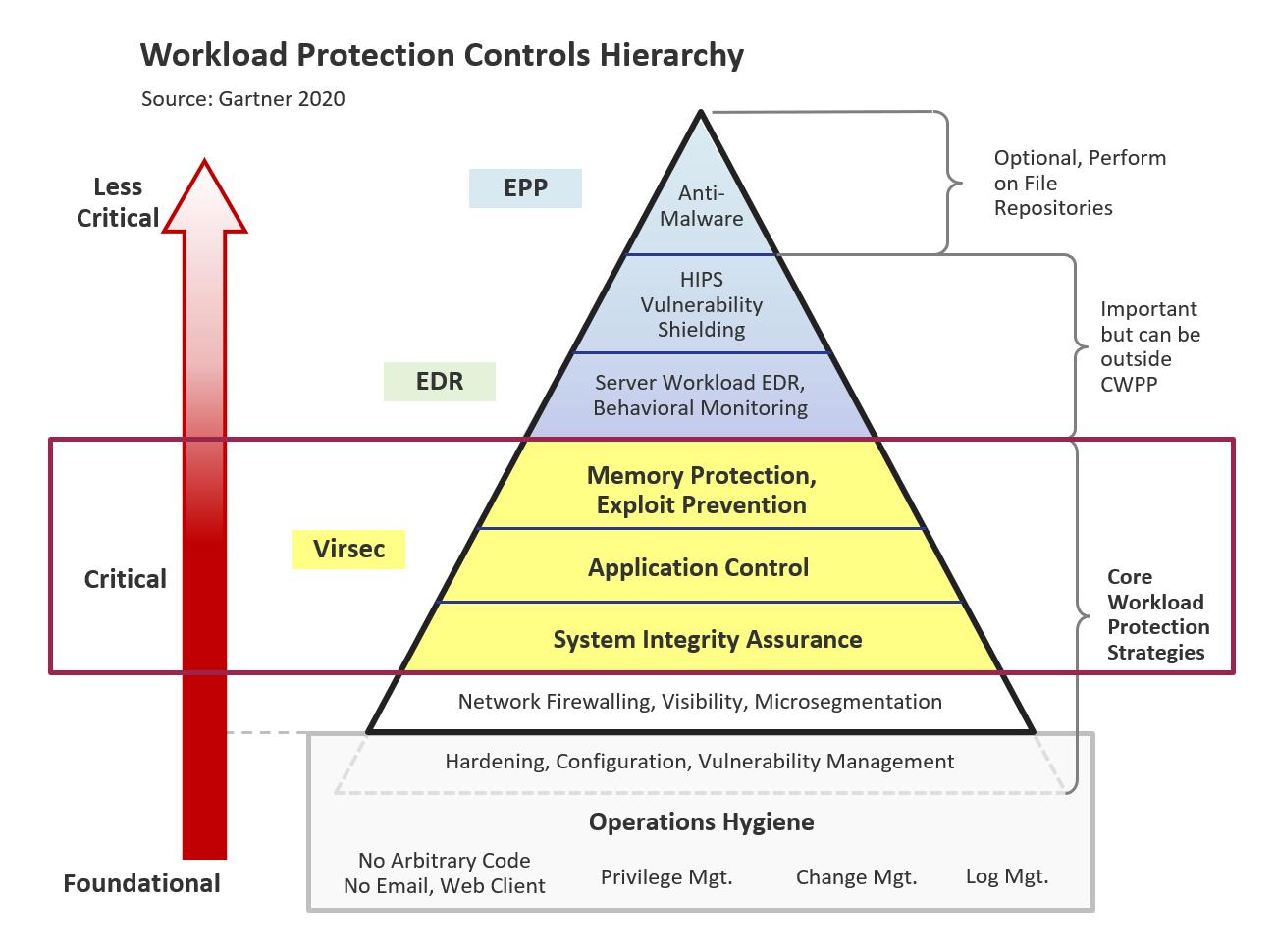
Virsec Addresses Critical Core Workload Protection Strategies
Gartner Market Guide for Cloud Workload Protection Platforms – 14 April 2020

Download the White Paper to learn more about Virsec's Runtime Application Protection
Workloads Are the New Attack Surface for Ransomware
Ransomware, espionage, sabotage, theft, fraud and other exploits are proliferating exponentially. The most insidious threats bypass traditional defenses and execute at the speed of code, often going undetected for days, weeks, months or even years. Organizations must assume that their networks already have the precursors to the next ransomware attack inside it.
The workloads themselves are the new attack surface. To effectively protect them, security solutions must include system assurance, application control and memory protection. Code that executes during runtime can be almost undetectable, and the traditional blacklisting approach cannot possibly detect all the malware that is generated each day. Adopting a positive security model and arming the workloads to defend themselves is the best protection against the most sophisticated and evasive ransomware attacks.
Download the Ransomware Solution Brief to learn more.
Eliminate Vulnerability Risk During Patching Cycles
The recent Log4j vulnerability has demonstrated very clearly that chasing and patching vulnerabilities is a never ending game of cat and mouse where the attacker always has the upper hand.
Patching software is a fact of life, but the avalanche of vulnerabilities and today’s complex software stacks makes it difficult to keep up. Many organizations fall behind in patching software because the process is too labor intensive, disruptive and causes unintended consequences, or simply because patches are not available. Meanwhile, attackers have the upper hand during the weeks, months, or years it takes to close the window on vulnerabilities.
Virsec eliminates the risk posed by disclosed or undisclosed vulnerabilities being exploited during lengthy patching cycles. By mapping and monitoring actual code execution, Virsec Security Platform (VSP) instantly identifies when an application is about to be targeted and stops attacks in their tracks. VSP delivers precise Compensating Security Controls that eliminate the risks of vulnerabilities being used to abuse web applications, third-party code, and legacy systems.
Virsec Ensures:
- Automated protection from disclosed or undisclosed vulnerabilities
- Compensating Security Controls eliminating vulnerability risks during patching cycles
- Inline protection for vulnerabilities discovered during testing
- Runtime protection for undisclosed vulnerabilities and zero-day threats preventing exploits from executing
Download the Solution Brief to learn more about Virsec's Virtual Patching Capabilities
SolarWinds Attack End-To-End Demo
Current security solutions rely on knowledge of past malware to form signatures or behavioral profiles of what might happen next. End point protection, perimeter and threat hunting tools won’t identify unique malware that already exists in your system.
Effective supply chain protection requires new tactics. Watch as the Virsec security solution immediately identifies and stops an evasive Remote Code Execution attack in an end-to-end recreation of the SolarWinds attack.
Florida Water Utility Cyberattack
It demonstrates how Virsec can protect CII’s SCADA systems at various stages of the cyber kill chain.
